Table of contents
- 1. Declarative Syntax:
- 2. Key Concepts:
- 3. Workflow:
- 4. State Management:
- 5. Dependency Management:
- 6. Workspaces:
- 7. Variable Files and Environments:
- 8. Terraform Modules:
- 9. Error Handling and Rollbacks:
- 10. Best Practices:
- Declarative vs. Imperative IaC:
- Configuration Management vs. Infrastructure as Code:
- Day 55: Understanding Configuration Management with Ansible
Infrastructure as Code (IaC) is a concept and practice that involves managing and provisioning computing infrastructure through machine-readable script files, rather than through physical hardware configuration or interactive configuration tools. The goal is to automate and streamline the process of deploying and managing infrastructure, making it more efficient, scalable, and repeatable.
Here are key aspects to understand about Infrastructure as Code:
Definition and Description:
Code Representation: Infrastructure as Code represents the desired state of your infrastructure using code. This code can be written in a domain-specific language or a general-purpose programming language.
Declarative vs. Imperative: IaC can be declarative, specifying the desired end state without detailing the step-by-step process (e.g., Ansible, Terraform), or imperative, where the code outlines the specific steps to reach the desired state.
Advantages:
Reproducibility: IaC enables the recreation of identical environments, reducing discrepancies between development, testing, and production.
Scalability: Automation allows for the efficient scaling of infrastructure up or down based on demand.
Consistency: IaC helps maintain consistency across environments, reducing configuration drift and the likelihood of errors.
Tools:
Terraform: A widely-used open-source IaC tool that supports multiple cloud providers and on-premises environments.
Ansible: An open-source automation tool that can be used for IaC, configuration management, and application deployment.
CloudFormation: An AWS-specific IaC service for defining and provisioning AWS infrastructure.
Workflow:
Version Control: Infrastructure code should be stored in version control systems (e.g., Git) to track changes and collaborate with team members.
Continuous Integration/Continuous Deployment (CI/CD): IaC fits well into CI/CD pipelines, automating the testing and deployment of infrastructure changes.
Components:
Templates: These are the code files that define the infrastructure, specifying resources, their configurations, and relationships.
Variables: Parameters and variables allow for flexibility and reusability in templates.
Modules: Encapsulating reusable components of infrastructure code makes it easier to manage and maintain.
Security and Compliance:
Auditing: IaC can facilitate auditing and compliance by providing a clear record of changes to infrastructure.
Security Best Practices: Following security best practices in your IaC ensures that security measures are applied consistently across environments.
Learning Resources:
Documentation: Each IaC tool has extensive documentation that provides guidance on syntax, features, and best practices.
Tutorials and Courses: Online tutorials and courses can help you get hands-on experience with IaC tools.

Terraform is a widely-used Infrastructure as Code (IaC) tool that allows you to define and provision infrastructure resources in a declarative manner. Here's a comprehensive overview of key concepts and practices related to Terraform:
1. Declarative Syntax:
- HCL (HashiCorp Configuration Language): Terraform uses HCL to define infrastructure as code. It is a declarative language that allows you to express the desired state of your infrastructure.
2. Key Concepts:
Providers: Terraform uses providers to interact with various infrastructure platforms (e.g., AWS, Azure, GCP). Each provider offers a set of resources that can be managed by Terraform.
Resources: Infrastructure components (e.g., virtual machines, networks, databases) are defined as resources in Terraform. Each resource type is associated with a specific provider.
Variables: Terraform supports the use of variables to parameterize configurations. Variables can be defined in separate files or passed in as command-line arguments.
Outputs: Outputs allow you to expose certain values from your Terraform configuration, making them accessible for use elsewhere or for display after provisioning.
Modules: Modules are reusable components that encapsulate a set of resources and configurations. They facilitate code organization and reuse across different parts of your infrastructure.
3. Workflow:
Initialize: Run
terraform initto initialize a Terraform configuration, which downloads the necessary provider plugins and sets up the working directory.Plan: Use
terraform planto preview the changes that Terraform will make to your infrastructure. It shows additions, modifications, or deletions of resources.Apply: Execute
terraform applyto apply the changes defined in your configuration. Terraform interacts with the API of the selected provider to create, update, or delete resources.Destroy: When resources are no longer needed,
terraform destroycan be used to remove them. It's crucial to be careful with this command as it irreversibly deletes resources.
4. State Management:
Terraform State: Terraform keeps track of the current state of your infrastructure in a state file. This file is used to understand the existing infrastructure and to determine the changes required for updates.
Remote State: Consider using remote state storage to share the state file among team members and maintain a centralized and consistent state.
5. Dependency Management:
- Implicit Dependencies: Terraform automatically determines the order of resource creation based on implicit dependencies. For explicit dependencies, use the
depends_onattribute.
6. Workspaces:
- Workspaces: Workspaces allow you to manage multiple environments (e.g., development, production) with separate state files, variables, and configurations.
7. Variable Files and Environments:
Variable Files: Separate variable files can be used to manage environment-specific configurations.
Environments: Leverage Terraform workspaces or directory structures to organize configurations for different environments.
8. Terraform Modules:
Module Structure: Modules encapsulate a set of resources and are defined in a directory with its own Terraform files.
Module Sources: Modules can be sourced from local paths, Git repositories, or Terraform Registry.
9. Error Handling and Rollbacks:
Error Handling: Terraform provides detailed error messages during the planning phase to help identify and address issues before applying changes.
Rollbacks: Terraform doesn't natively support rollbacks, but version control, backups, and careful planning can help mitigate issues.
10. Best Practices:
Version Control: Use version control systems like Git to track changes to your Terraform code.
Secure Variables: Utilize Terraform Vault or other secure methods for managing sensitive data like API keys and passwords.
Review and Test: Regularly review and test your Terraform configurations to catch errors and ensure they align with the desired state.
Declarative vs. Imperative IaC:
Declarative: Describes the desired state without specifying the step-by-step process. Tools like Terraform use a declarative approach, allowing users to define what the infrastructure should look like, and the tool handles the provisioning details.
Imperative: Specifies the exact steps to reach the desired state. Tools like Ansible use an imperative approach, where you define a series of tasks to be executed in a specific order.
Configuration Management vs. Infrastructure as Code:
Configuration Management: Focuses on maintaining the desired state of software on existing servers. Tools like Ansible, Puppet, and Chef fall under this category.
Infrastructure as Code: Focuses on defining and provisioning infrastructure resources, including servers, networks, and storage. Tools like Terraform and AWS CloudFormation are IaC tools.
Day 55: Understanding Configuration Management with Ansible
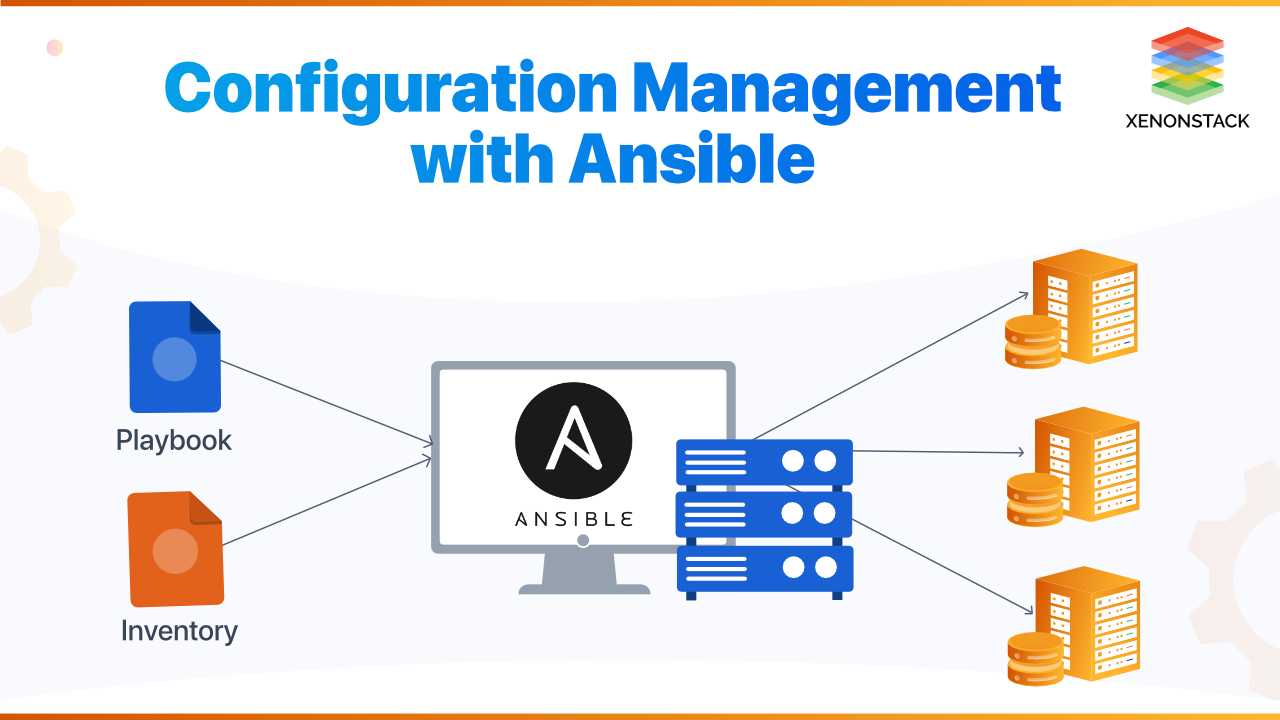
Configuration Management with Ansible involves using Ansible, an open-source automation tool, to define and enforce the desired state of systems and applications. Ansible enables you to automate the configuration, deployment, and management of infrastructure, making it a powerful tool for maintaining consistency across environments. Here's an overview of key concepts and practices related to Configuration Management with Ansible:
1. Key Concepts:
Playbooks: Ansible configuration files written in YAML that define a set of tasks to be executed on remote hosts. Playbooks describe the desired state of a system.
Roles: Organizational units in Ansible that encapsulate tasks, variables, and handlers in a directory structure. Roles promote reusability and modularization of configuration code.
Inventory: A file or collection of files that specify the hosts on which Ansible tasks will be executed. It defines groups of hosts and their attributes.
Modules: Ansible modules are units of code that perform specific tasks, such as managing packages, files, services, and more. Modules are executed on remote hosts.
Tasks: Actions defined in Ansible playbooks to achieve a specific configuration state. Tasks use Ansible modules to interact with the system.
Facts: System information gathered by Ansible about the target hosts. Facts can be used in playbooks to make decisions based on the current state of the system.
2. Workflow:
Define Playbooks: Write Ansible playbooks to specify the desired configuration of systems. Playbooks include tasks that are executed sequentially.
Inventory Setup: Create an inventory file listing the hosts that Ansible will manage. Define variables, groups, and group variables in the inventory.
Run Ansible Commands: Execute Ansible commands or playbooks to apply configurations to the target hosts. Ansible communicates with hosts via SSH.
Idempotency: Ansible is designed to be idempotent, meaning that running a playbook multiple times has the same result as running it once. This ensures that the system converges to the desired state, regardless of its current state.
3. Roles and Reusability:
Organizing Code: Use roles to structure your Ansible code in a modular way. Roles consist of tasks, handlers, variables, and other files organized in a directory structure.
Role Dependencies: Roles can depend on other roles, allowing you to build on existing roles and create a hierarchy of configurations.
4. Dynamic Inventories:
Dynamic vs. Static: Ansible inventories can be static, defined in a file, or dynamic, generated by external scripts or plugins. Dynamic inventories allow for more flexibility in managing hosts.
Cloud Providers: Ansible can dynamically discover and manage hosts in cloud environments like AWS, Azure, or Google Cloud.
5. Variable Management:
Global vs. Playbook Variables: Define variables at different levels, such as globally, within playbooks, or within roles. Variables can be used to customize configurations for different environments or hosts.
Variable Precedence: Understand the order of precedence for variables to manage conflicts and ensure that the desired values are applied.
6. Handlers:
- Handlers in Playbooks: Handlers are tasks that are triggered by other tasks, typically in response to changes. For example, restarting a service after a configuration file is updated.
7. Tags and Conditionals:
Tags: Assign tags to tasks in playbooks to selectively run or skip specific tasks. This is useful for partial playbook execution.
Conditionals: Use conditional statements in playbooks to make decisions based on facts, variables, or other criteria.
8. Roles and Ansible Galaxy:
Ansible Galaxy: A hub for finding, sharing, and reusing Ansible roles. Use Ansible Galaxy to discover and install roles contributed by the community.
Role Development Best Practices: Follow best practices when developing roles, such as keeping roles independent, documenting usage, and using role testing tools.
9. Security Considerations:
SSH Key Management: Ansible relies on SSH for communication. Ensure proper management and security of SSH keys for connecting to remote hosts.
Vault for Secrets: Ansible Vault allows you to encrypt sensitive data, such as passwords or API keys, within playbooks or roles.
10. Integration with CI/CD:
Continuous Integration: Integrate Ansible playbooks into CI/CD pipelines to automate the testing and deployment of configurations.
Testing Environments: Use tools like Molecule to test roles and playbooks in isolated environments, ensuring reliability and correctness.
Ansible: -

Ansible is an open-source automation tool designed for configuration management, application deployment, task automation, and IT orchestration. Developed by Red Hat, Ansible simplifies complex infrastructure management tasks by providing a simple, human-readable language to describe automation processes.
1. Key Concepts:
Playbooks: Ansible playbooks are written in YAML and define a set of tasks to be executed on remote hosts. Playbooks describe the desired state of the system.
Modules: Ansible modules are small, self-contained scripts that perform specific tasks on target systems. Modules can manage files, packages, services, and more.
Inventory: Ansible uses an inventory file to define and organize the hosts on which tasks will be executed. It supports both static and dynamic inventories.
Roles: Roles are a way of organizing playbooks and other files in a structured manner. Roles help in promoting reusability and maintainability of Ansible code.
Tasks: Tasks are the individual units of work in an Ansible playbook. Each task calls a specific module with defined parameters.
2. Workflow:
Inventory Setup: Define hosts in the inventory file, organizing them into groups and specifying variables as needed.
Playbook Creation: Write Ansible playbooks that describe the desired configuration or tasks to be executed on hosts.
Execution: Run Ansible commands or playbooks to apply configurations to remote hosts. Ansible communicates with hosts over SSH.
Idempotency: Ansible playbooks are designed to be idempotent, meaning running them multiple times has the same result as running them once, ensuring consistent states.
3. Modules and Tasks:
Module Types: Ansible includes a wide range of modules for various tasks, including system management, cloud resource provisioning, and application deployment.
Ad-Hoc Commands: Ansible allows for running ad-hoc commands for quick tasks without the need for a playbook.
Handlers: Handlers are tasks triggered by other tasks. They are often used for actions like restarting a service after a configuration change.
4. Variables and Facts:
Variables: Ansible allows the use of variables to make playbooks more flexible and reusable. Variables can be defined in playbooks, inventory, or external files.
Facts: Ansible collects system information known as facts. Facts can be used within playbooks to make decisions based on the current state of the system.
5. Roles and Includes:
Roles: Roles provide a way to organize and structure Ansible code. They encapsulate tasks, handlers, variables, and other files in a defined directory structure.
Include Statements: Use
includestatements to reuse tasks or playbooks within other playbooks.
6. Conditionals and Loops:
Conditionals: Ansible playbooks support conditional statements to make decisions based on facts, variables, or other criteria.
Loops: Loops allow for the repetition of tasks, simplifying the playbook code.
7. Templates and Files:
Templates: Ansible templates use Jinja2 syntax to dynamically generate configuration files based on variables.
Files: Copy files from the local machine to remote hosts using the
copymodule.
8. Dynamic Inventories:
- Dynamic Inventory Scripts: Ansible can use dynamic inventories generated by scripts or external tools to dynamically discover and manage hosts.
9. Roles and Ansible Galaxy:
Ansible Galaxy: Ansible Galaxy is a platform for sharing, discovering, and downloading Ansible roles. It simplifies the reuse of community-contributed roles.
Role Development Best Practices: Follow best practices when developing Ansible roles, such as modularization, documentation, and testing.
10. Security Considerations:
SSH Key Management: Ansible uses SSH for communication. Proper management and security of SSH keys are crucial.
Vault for Secrets: Ansible Vault allows for encrypting sensitive data within playbooks, ensuring secure handling of passwords and other confidential information.
11. Integration with CI/CD:
Continuous Integration: Integrate Ansible playbooks into CI/CD pipelines to automate testing and deployment processes.
Testing Environments: Tools like Molecule can be used to test Ansible roles in isolated environments for reliability.
.
.
.
.
🙌 Thank you for reading my blog! 🚀 If you found this information helpful, drop a comment and spread the knowledge! 🔍 For more Kubernetes insights and updates, feel free to follow me on:
LinkedIn: Sumit Katkar 🌐
HashNode: Sumit Katkar's Blog 📝
Happy Learning! 🎉
